Health
Insurance
Portability
&
Accountability
Act
HIPAA. A necessary evil in the world of healthcare in the digital age. Necessary because it protects the privacy and safety of millions of individual’s Personal Health Information (PHI). Evil because your organization will spend a lot of time and money on making sure you comply to the rule.
HIPAA is composed of three main sections. The privacy rule, the security rule, and the breach notification rule. Below we discuss each of these rules.
Privacy Rule
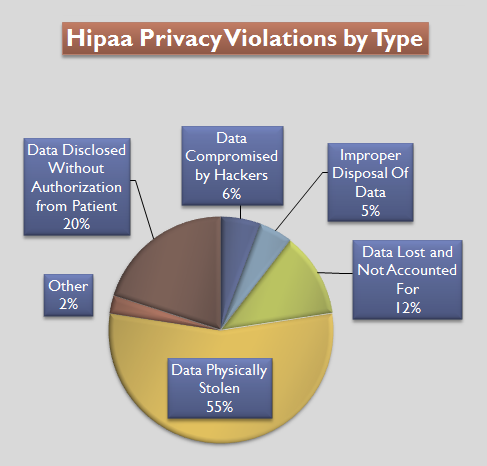
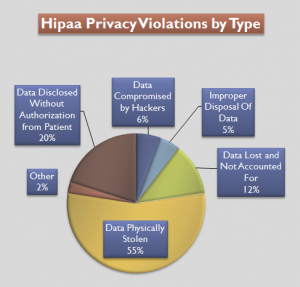
The privacy rule protects individual’s medical records and personal health information (PHI).
PHI is any data that expresses health status, provision of health care, or payment for health care that can be linked to an individual.
The privacy rule protects PHI by:
- Applying safeguards (ex. minimum disclosure, communication preferences such as not calling at work, etc.)
- Enacting limits and conditions on the uses and disclosures without patient authorization
- Allowing patients to examine and obtain a copy of their health records
- Allowing patients to request corrections to health records
The rule applies to:
- Health care
- Health care providers
- Health plans
- Health care clearinghouses
- Health care providers that conduct certain health care transactions electronically
- Health Insurers
- Independent contractors of covered entities who fit within the definition of “business associates”
- Hybrid entities that perform both covered and non-covered functions as part of its business operations
To comply, health organizations (or covered entities) must:
- Notify individuals of uses of their PHI
- Keep track of disclosures of PHI and document privacy policies and procedures
- Appoint a Privacy Official and a contact person responsible for receiving complaints
- Train all members of their workforce in procedures regarding PHI
PHI may be disclosed under the following situations:
- The very minimum PHI may be disclosed to facilitate treatment, payment, or health care operations without a patient’s express written authorization
- As required by law (court orders, court-ordered warrants, subpoenas)
- To identify or locate a suspect, fugitive, material witness, or missing person
Security Rule
Complimentary to the privacy rule, the security rule protects PHI that is in electronic form, or Electronic Personal Health Information (EPHI). The security rule places administrative, technical, and physical safeguards on EPHI. Below are some examples of administrative, technical, and physical safeguards that must be put in place.
Administrative
Administrative controls are “policies and procedures designed to clearly show how the entity will comply with the act”
For example, this can include:
- Development of a written plan outlining privacy procedures
- Designating an individual as a privacy/HIPAA compliance officer
- Ensuring employees who only have a “need to know” have access to PHI
- A process for authorizing , establishing, and modifying access for employees, as well as how to terminate access to information
- Offering ongoing training
- Ensuring third-party compliance
- Contingency plan development
- Internal audits
- Security breach response plan
Technical
Technical controls control “physical access to protect against inappropriate access to protected data.” These technical controls include requirements for:
- Data encryption
- Unauthorized change alerts
- Data corroboration and methods to check data integrity
- Authenticating users
- Documented practices & procedures
- Configuration setting tracking & management
- Risk analysis & management plans
Physical
Physical controls control “access to computer systems and enabling covered entities to protect communications containing PHI transmitted electronically over open networks from being intercepted by anyone other than the intended recipient”
- Proper disposal of equipment
- Proper scanning of equipment prior to addition to network
- Limiting, controlling, and monitoring of authorized users access to hardware and software
- Signing in of all visitors
- Development of a physical security plan
- Ensuring devices and screens are placed out of view by passerby’s
Breach Notification Rule
The breach notification rule requires that “HIPAA covered entities and their business associates to provide notification following a breach of unsecured protected health information.”
What a Breach Is and Is Not
A breach is defined as “impermissible use or disclosure under the Privacy Rule that compromises the security or privacy of the protected health information.”
A breach does not have to be reported if there low probability that PHI has been compromised based on a risk assessment of at least the following factors:
- The nature and extent of the protected health information involved, including the types of identifiers and the likelihood of re-identification;
- The unauthorized person who used the protected health information or to whom the disclosure was made;
- Whether the protected health information was actually acquired or viewed; and
- The extent to which the risk to the protected health information has been mitigated.
Notification of a breach should be made as soon as possible and no later than 60 days after the breach occurred.
Breaches can be reported in the following ways
- Individual Notice
- Media Notice
- Notice to Secretary
- Posting on HHS Public Website
Acronym Roundup
HIPAA – Health Insurance Portability and Accountability Act
PHI – Personal Health Information
EPHI- Electronic Personal Health Information
Advanced Resources:
HIPAA Privacy Rule (PDF)
Who does the privacy rule apply to?